Phish Report Integration with Microsoft Defender
Boxphish supports the use of the built-in Microsoft Outlook phish reporting capability provided by Defender. Once configured any email reported as phishing will be deleted from the User's inbox and s…
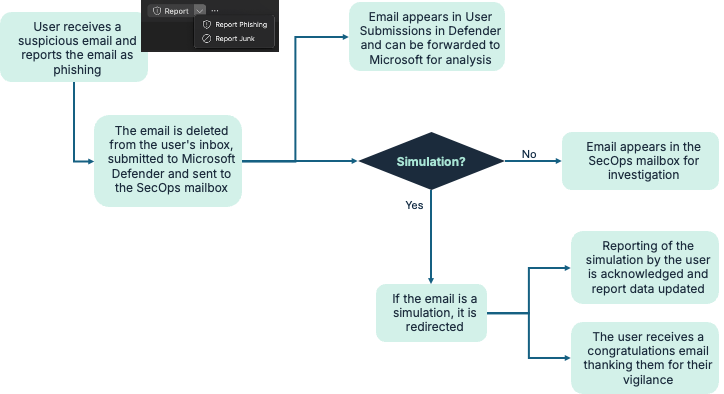
Boxphish supports the use of the built-in Microsoft Outlook phish reporting capability provided by Defender. Once configured any email reported as phishing will be deleted from the User's inbox and submitted to Defender and optionally Microsoft for analysis. Furthermore, if the email is a phishing simulation from Boxphish the following will happen:
- The email will not reach the SecOps mailbox as it does not require internal investigation. However it will appear in the submissions section in Defender.
- The User will be sent a congratulations email based on a customisable template thanking them for being vigilant and reporting a phishing email.
- The phishing simulation reported will be marked as such within the Boxphish system and be presented in the reports for that user.
How does the Phish Report Integration work?
The Phish Report integration empowers users to report any email they are suspicious of to their IT team, and for the IT team to make full use of Microsoft Defender's email reporting capabilities. The Boxphish phishing simulations will be seamlessly removed from the SecOps investigation mailbox and processed by Boxphish separately.
The diagram below shows the logical flow of the integration.
How to configure the Microsoft Phish Reporting tool
Part 1: Defender Configuration
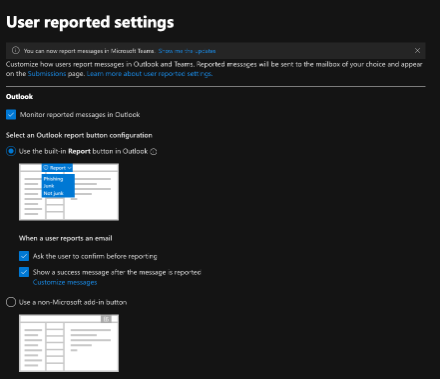
- Navigate to the User Reported Settings within Defender at the following location: https://security.microsoft.com/securitysettings/userSubmission
- Enable the button by checking the 'Monitor reported messages in Outlook' and select 'Use the built-in Report button in Outlook' as per the screenshot below:
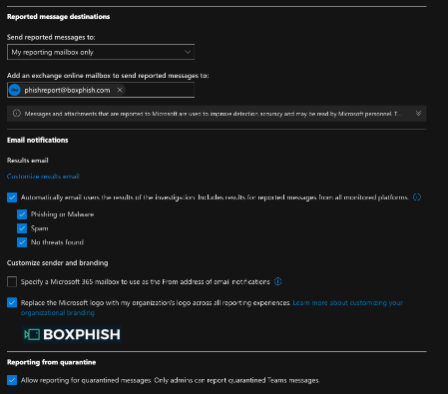
- Set the 'Reported message destinations' as follows and shown in the screenshot:
- Set 'Send reported messages to:' 'My reporting mailbox only' or 'Microsoft and my reporting mailbox'.
- Populate the 'Add an exchange online mailbox to send reported messages to:' with the email address of your SecOps mailbox.
- The remaining settings may be configured as desired. For full details refer to the Microsoft documentation here
Part 2: Exchange Transport Rule
- Navigate to the Transport rules section of the Microsoft Exchange Admin Centre at the following location: https://admin.exchange.microsoft.com/#/transportrules
- Select 'Add a rule' and a pop-up will appear
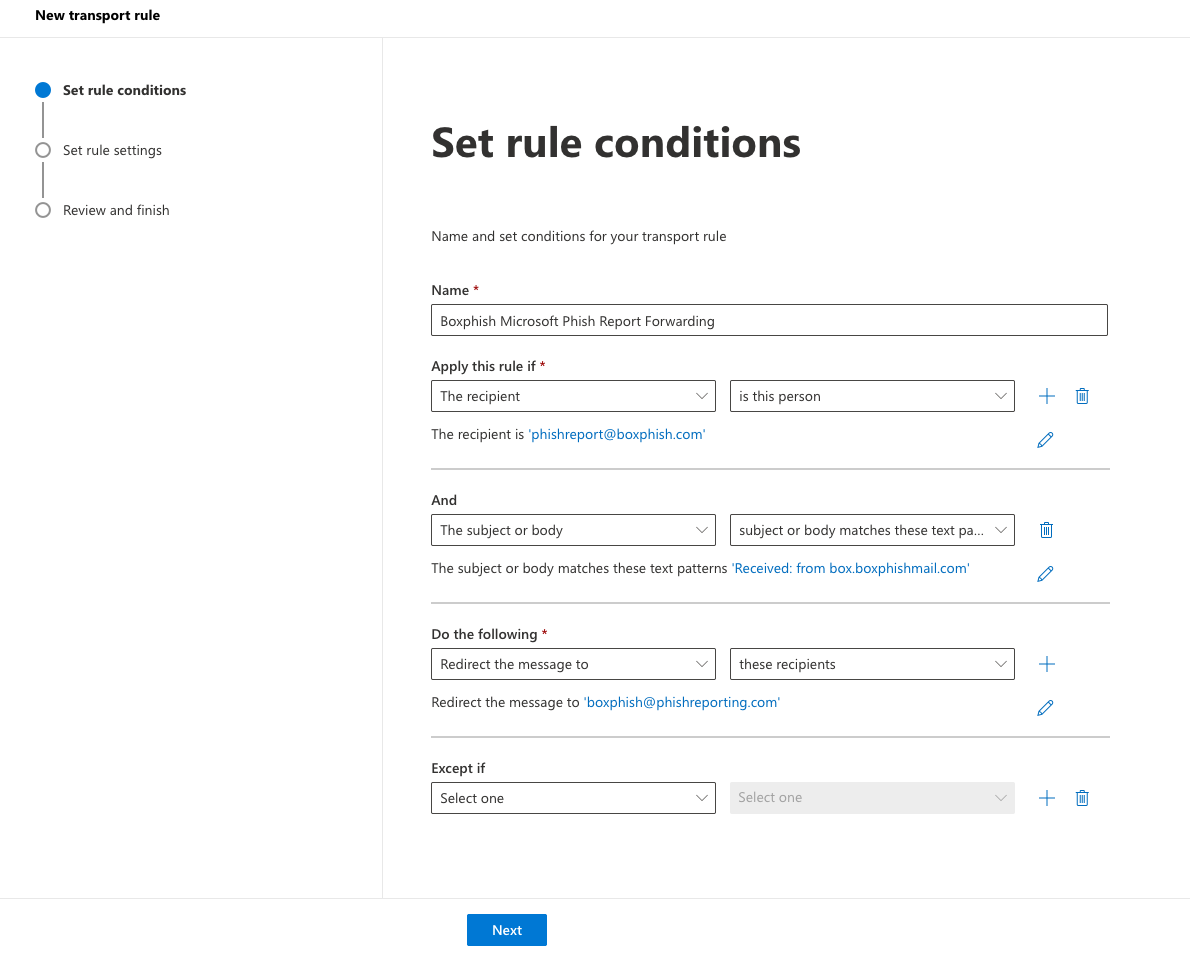
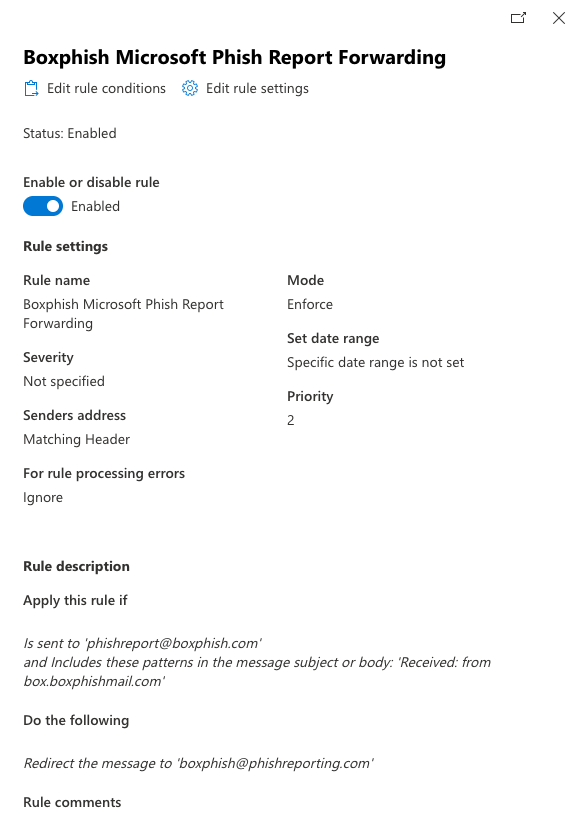
- Give the rule a meaningful name, for example 'Boxphish Microsoft Phish Report Forwarding'
- Set the 'Apply this rule if' logic as 'The recipient' and 'is this person' and then select the mailbox configured in Defender as the reporting mailbox.
- Add a second condition as 'The subject or body' and 'subject or body matches these text patterns' and then enter the text 'Received: from box.boxphishmail.com'.
- In the 'Do the following' section add select 'Redirect the message to' and 'these recipients' and then enter 'boxphish@phishreporting.com' as the recipient.
- Leave the 'Except if' section empty.
- The screen should look like the below. Once done click Next.
- On the 'Set the rule settings' page leave the settings as the default and click next.
- Review the rule and click finish. The rule will now be created, which may take a few seconds.
- Once saved, the rule will need to be enabled. Select the newly created rule and toggle the 'Enable or disable rule' toggle to 'Enabled'. You may also need to increase the priority of the rule by clicking the 'Edit rule settings' and setting an appropriate priority level based on your existing rules. The final configuration should appear like the screenshot below:
Benefits of using Defender
When you submit a phishing email to Microsoft Defender, you're helping Microsoft improve its threat intelligence and email protection systems. Below is a summary of the main benefits:
- Improve the accuracy of spotting real phishing attacks by Microsoft Defender for Office 365
- Update Microsoft’s email filtering rules and threat detection algorithms
- Provide faster protection across the ecosystem (e.g., Microsoft 365 users)
What happens after submission
- Microsoft analyses the email’s content, headers, and attachments
- If verified as phishing/malicious:
- Microsoft updates filters to block similar threats
- The email may also be removed from other users’ inboxes (zero-hour auto purge)
- You may get a submission status/report in the Defender portal
Benefits for Organisations
- Enhances real-time protection in Defender for Office 365
- Contributes to user-reported insights for attack campaigns
- Allows security teams to track trends and response actions in the Submissions dashboard
How did we do?
Collections
